In today’s digital landscape, where cyber threats loom large and data breaches can have devastating consequences, effective security controls management is paramount for modern organizations. Security controls encompass a range of measures designed to safeguard sensitive information, protect against unauthorized access, and mitigate risks to the organization’s assets and reputation. From firewalls to encryption protocols, these controls form the backbone of a robust cybersecurity strategy, ensuring the confidentiality, integrity, and availability of critical data.
However, managing these security controls manually can be a daunting task, especially as organizations grapple with ever-evolving threats and complex regulatory requirements. This is where the concept of automating security controls management comes into play. By leveraging automation technologies, organizations can streamline routine security tasks, improve response times to security incidents, and enhance overall operational efficiency.
For CISOs, automation offers a powerful tool to adapt and scale their security practices in the face of evolving threats and growing organizational needs. Automation allows CISOs to allocate resources more effectively, prioritize security initiatives, and stay ahead of emerging risks, ultimately enabling them to better protect their organizations in an increasingly digital world.
Challenges CISOs encounter while managing security controls
Managing Complexity: CISOs face the challenge of managing a complex array of security controls across multiple tools and platforms, often leading to inconsistencies and gaps in coverage.
● Resource Constraints: According to a study by cybersecurity ventures there is an estimated global cybersecurity workforce gap of 3.4 million. These resource constraints pose a significant challenge for CISOs, making it difficult to implement and maintain effective security controls manually.
● Rapidly Evolving Threat Landscape: CISOs must contend with a constantly evolving threat landscape, with new attack vectors and vulnerabilities emerging regularly, making it challenging to keep pace with manual security controls management.
● Human Error: Manual management of security controls is prone to human error, such as misconfigurations or oversight, which can leave organizations vulnerable to cyber threats. As per a Gartner report, by 2025, more than half of significant cyber incidents will come from a lack of talent as well as general human error.
● Compliance Burdens: Meeting compliance requirements is a major challenge for CISOs, as manual management of security controls often results in labor-intensive audit processes and the risk of non-compliance.
● Lack of Scalability: Traditional methods of managing security controls are not easily scalable to meet the needs of growing organizations or adapt to changing threat landscapes.
● Inefficient Incident Response: Manual processes hinder incident response efforts, as CISOs must manually identify and remediate security incidents, leading to delays in detection and response times.
● Inadequate Visibility: Manual management of security controls may result in limited visibility into the organization's security posture, making it difficult for CISOs to identify and address potential risks effectively.
The Role of Automation
Automation plays a pivotal role in modern security controls management, revolutionizing the way organizations defend against cyber threats. Here’s a closer look at the role of automation in enhancing security practices:
Introduction to Automation: In the context of security controls management, automation streamlines various processes, from monitoring network activity to analyzing security logs, enabling organizations to respond to threats more effectively and efficiently.
Streamlining Repetitive Tasks: One of the primary benefits of automation is its ability to streamline repetitive tasks that are essential for maintaining a strong security posture. Tasks such as patch management, user access provisioning, and security policy enforcement can be automated, freeing up security teams to focus on more strategic initiatives.
Machine Learning and Artificial Intelligence (AI): Machine learning and AI play a crucial role in security automation by enabling systems to learn from data, identify patterns, and make intelligent decisions autonomously. These technologies power advanced threat detection and response capabilities, allowing organizations to detect and mitigate threats in real-time.
Specific Security Controls: Several security controls can be automated to improve overall security posture. Some examples include:
● Automated Vulnerability Management: Automating security controls can help prevent a significant number of attacks by patching vulnerabilities, detecting suspicious activity, and enforcing security policies.
● Security Orchestration and Automation Response (SOAR): SOAR platforms automate incident response processes, including threat detection, analysis, and response, accelerating incident resolution and reducing manual effort.
● Identity and Access Management (IAM): Automation can streamline user access provisioning and deprovisioning processes, ensuring that users have appropriate access levels while reducing the risk of unauthorized access.
Automation in security controls management not only enhances efficiency but also enables organizations to adapt and scale their security practices to meet evolving threats and business needs. By leveraging automation technologies, organizations can strengthen their defenses, improve incident response capabilities, and stay ahead of cyber threats in an increasingly digital world.
Benefits of Automating Security Controls Management
Automating security controls management offers a multitude of benefits for organizations seeking to bolster their cybersecurity defenses. Here are the key advantages:
Improved Efficiency and Productivity:
- Automation streamlines routine tasks, freeing up security teams to focus on more strategic initiatives. As per an article by Security Magazine, 41% of cybersecurity leaders believe that automation is the main driver in improving operational efficiency.
- Security personnel can also allocate their time and resources more effectively, leading to increased productivity and faster response times to security incidents.
Enhanced Accuracy and Consistency:
- Automated processes ensure consistency in applying security controls across the organization’s infrastructure.
- By eliminating manual intervention, automation reduces the risk of human error, ensuring that security policies are enforced accurately and consistently.
Rapid Threat Detection:
Automated security controls management helps continuously monitor network traffic, logs, and various data sources and platforms in real-time, swiftly identifying suspicious activities or anomalies to mitigate threats proactively.
Efficient Vulnerability Management:
Automation assists in identifying and prioritizing vulnerabilities in software and systems through signals from your other security tools, automating patching and updating processes can shrink the window of opportunity for attackers.
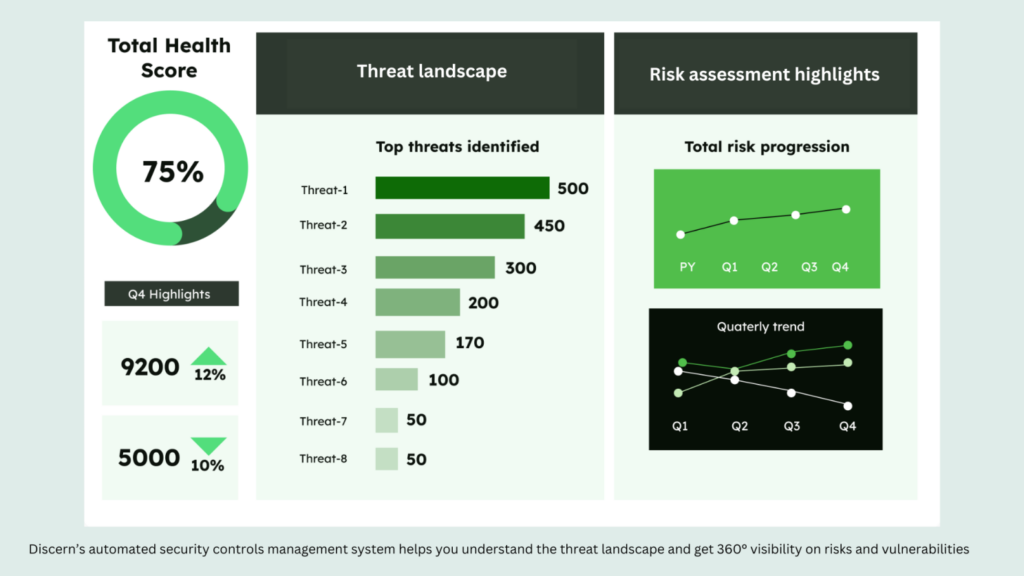
Phishing and Malware Defense:
Automated security controls and policy management can help security teams swiftly detect and thwart phishing attacks and malware distribution by scrutinizing email content, attachments, and URLs in real-time.
Accelerated Incident Handling:
Keeping the security controls and policy management automated expedites incident response by executing predefined actions in response to specific events. This may involve isolating compromised systems, blocking malicious IP addresses, and initiating predetermined incident response protocols.
Compliance and Reporting:
Automation ensures consistent enforcement of security policies and configurations throughout the organization, streamlining compliance management, and automating security report generation for audits and regulatory requirements.
Scalability to Adapt to Change:
- Automated security controls management provides scalability to adapt to changing organizational needs and evolving threat landscapes.
- Organizations can easily scale their security operations in response to growth, acquisitions, or changes in business priorities without the need for significant manual intervention.
Cost Savings:
- Automation leads to cost savings by reducing the need for manual labor and increasing operational efficiency.
- Organizations can achieve significant cost savings over time by automating repetitive tasks, minimizing the need for additional staffing, and reducing the risk of costly security breaches.
Automating security controls management not only enhances efficiency, accuracy, and scalability but also leads to significant cost savings and reduced security risks for organizations, ultimately strengthening their overall cybersecurity posture in an increasingly complex threat landscape.
Implementation Considerations
Implementing automated security controls management requires careful planning and consideration of various factors to ensure a smooth and effective transition. Here are the key implementation considerations:
Factors to Consider:
- Understand organizational goals and objectives related to security controls management.
- Assess current security processes and identify areas that can benefit from automation.
- Define clear metrics for success and establish key performance indicators (KPIs) to measure the impact of automation.
Integration with Existing Infrastructure:
- Ensure compatibility and seamless integration with existing security infrastructure and tools.
- Evaluate the interoperability of automated solutions with other security technologies to avoid compatibility issues and maximize efficiency.
Training and Upskilling Requirements:
- Provide comprehensive training and upskilling programs for security teams to familiarize them with automated tools and technologies.
- Invest in ongoing education and professional development to keep security professionals updated on the latest automation trends and best practices.
Compliance Considerations:
- Understand compliance requirements and regulatory frameworks relevant to the organization’s industry and geographic location.
- Ensure that automated security controls management solutions comply with relevant regulations, standards, and frameworks, such as GDPR, HIPAA, PCI DSS, etc.
- Implement appropriate controls and mechanisms to maintain compliance and address audit requirements effectively.
Regulatory Requirements:
- Consider regulatory requirements and industry-specific standards when designing and implementing automated security controls.
- Ensure that automated processes adhere to regulatory guidelines and incorporate necessary controls to protect sensitive data and maintain compliance.
By carefully considering these factors and addressing implementation considerations, organizations can successfully deploy automated security controls management solutions that enhance efficiency, improve security posture, and mitigate risks effectively.
Future Trends and Predictions
As technology continues to evolve, the landscape of security automation is poised for significant advancements. Emerging trends in security automation are shaping the future of cybersecurity practices, with several predictions indicating a transformative journey ahead.
Emerging Trends:
- Increased adoption of AI and machine learning algorithms for advanced threat detection and response. As per IBM’s AI and Automation for Cybersecurity Report, 64% of respondents have implemented AI for security capabilities.
- Integration of security orchestration, automation, and response (SOAR) platforms to streamline incident response workflows.
- Growth in the use of cloud-native security solutions to protect dynamic and distributed IT environments.
- Expansion of DevSecOps practices, integrating security controls into the software development lifecycle.
Predictions for the Future:
- Continued convergence of security tools and technologies into unified platforms for holistic security management.
- Enhanced automation capabilities leveraging predictive analytics to proactively identify and mitigate security risks.
- Rise of autonomous security systems capable of self-learning and adapting to evolving threats in real-time.
These future trends and predictions underscore the transformative potential of automated security controls management in shaping the future of cybersecurity practices. As organizations continue to embrace automation and leverage cutting-edge technologies, they will be better equipped to adapt and respond to evolving cyber threats in an increasingly digital world.
Maximizing the Impact of Automated Security Controls Management with Discern
Think of Discern Security as an advisor or assistant that analyzes and optimizes your security controls in real-time, while also facilitating cross-platform intelligence across all your security platforms, by creating a cybersecurity mesh.
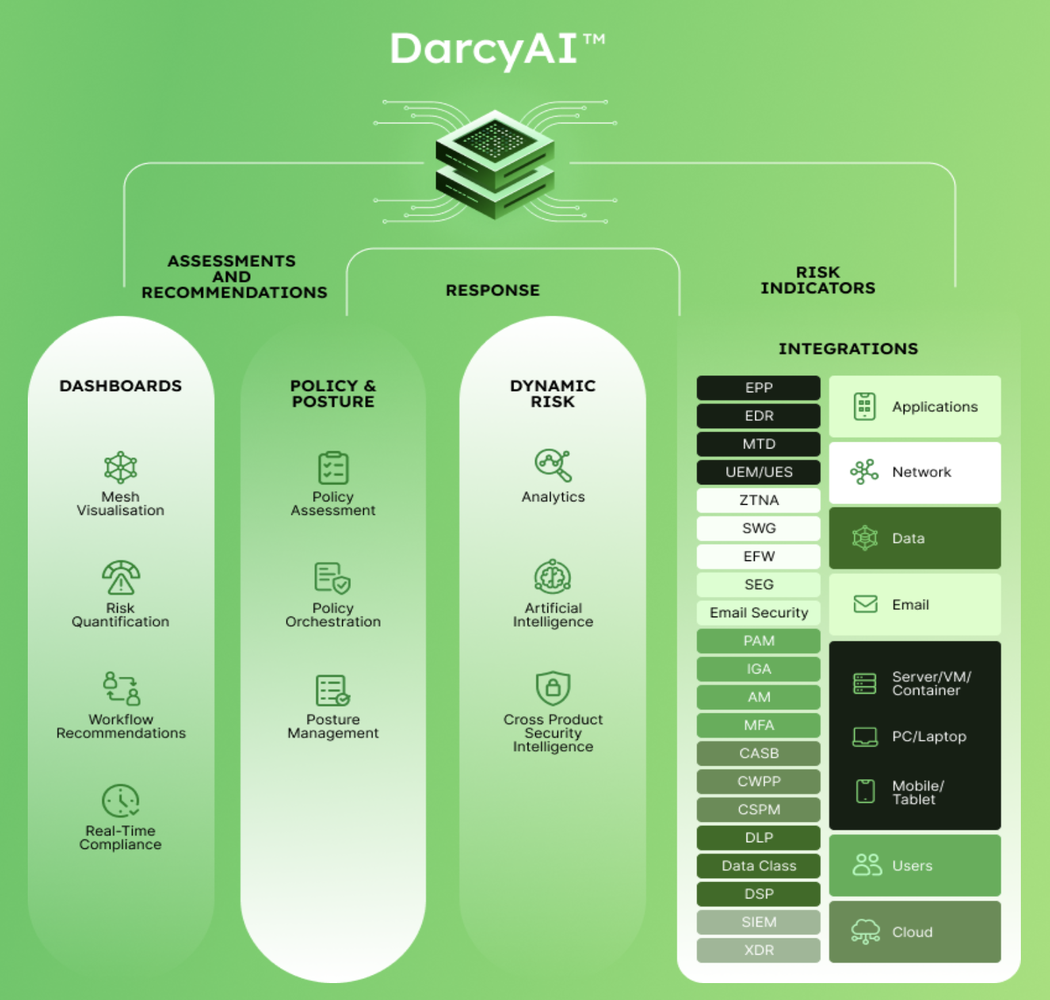
Here's how Discern uses cutting edge generative AI and the power of automation to keep your security controls up-to-date and help you proactively identify and remediate threats and vulnerabilities.
- Establishes baseline for security controls and configurations by seamlessly integrating with major security platforms covering EDR, SASE, Email, IAM, and others, assessing current security posture and identifying gaps in protection.
- Meticulously scores each security deployment in real-time, evaluating the effectiveness of controls and associated risk factors.
- Utilizes advanced generative AI to address critical security queries, providing answers and a roadmap for improvement.
- Dynamically maps security controls to established frameworks like MITRE, CIS, and NIST ensuring compliance and showcasing progress and ROI on security investments.
- Conducts health checks to ensure controls are up-to-date against ransomware threats, utilize latest vendor features, and maintain comprehensive coverage, facilitating swift deployment of configuration changes and optimizing overall security posture.
- Provides metrics, actionable insights, and personalized configuration recommendations tailored to department and target users, which gets implemented automatically by triggering the right workflows.
- Offers reporting dashboards to visualize risk, identify coverage gaps, top risks, and configuration optimization opportunities, aiding in cost savings.
Conclusion
Automating security controls management is crucial for organizations to navigate today's dynamic threat landscape. By seamlessly integrating with major security platforms and utilizing advanced AI powered platforms like Discern, CISOs can assess and improve their security posture, ensure compliance, and make informed decisions. Proactive assessments, dynamic mapping of controls, and personalized configuration recommendations enable swift deployment of changes and enhance overall security.





