Manage your
policies and
security posture
holistically
Get continuous health assessments, targeted insights and a 360° view of your EPP, EDR, Web security, IAM, PAM and more.
Challenges CISOs face with disjointed cybersecurity tools and products

1
2
3
4
Challenges in manually fine-tuning controls and policies
across different security tools, leading to potential gaps in the organization's security posture.
Limited granular understanding of each tool
coupled with scarcity of skilled cybersecurity professionals results in the suboptimal use of existing tools, compromising their effectivenes.
The absence of standardized metrics
makes it challenging for CISOs to showcase and quantify progress in their cybersecurity program
Our approach
We elevate your security resilience through our integrated security assessment and management solutions. Our dynamic risk assessment and automated remediation capabilities empower your security ecosystem, ensuring proactive defense against all emerging threats.
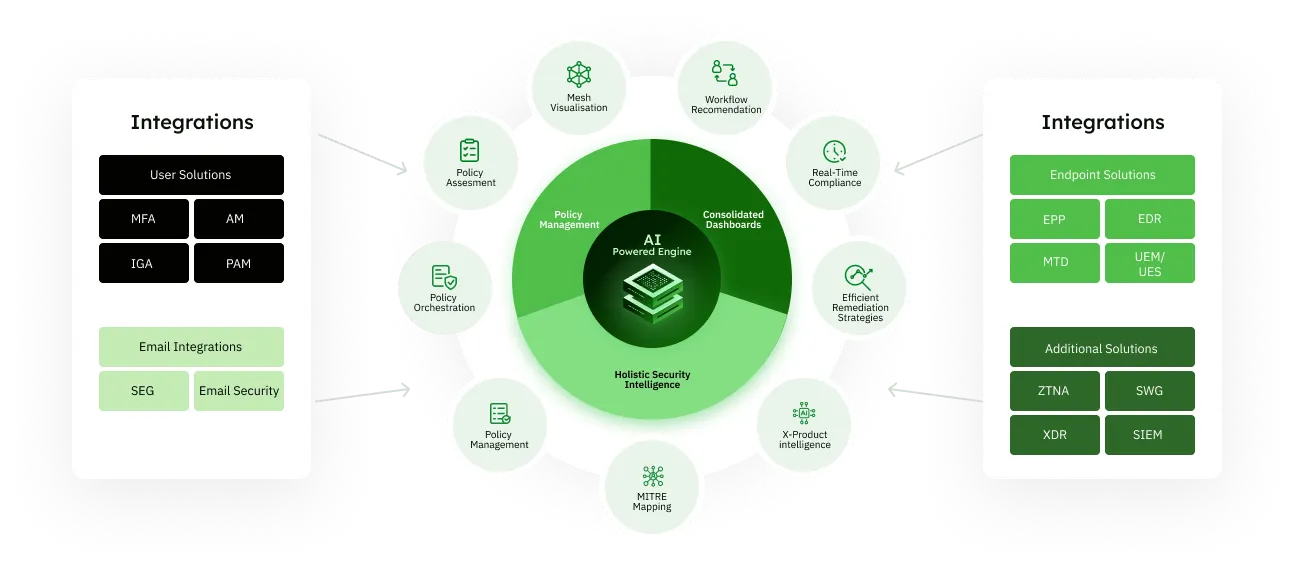
Solutions we offer

Endpoint Health Assessment
- Identify the top 10 Endpoint security configuration risks for your organization.
- Increase utilization of your existing EPP/ EDR and UEM vendors.
- Implement "risk-based controls" for the top 5% of users contributing to 80% of endpoint risks.
Web Security Health Assessment
- Evaluate the percentage of critical controls currently implemented in your web gateway, and receive tailored recommendations highlighting key controls to activate for enhancing the security of your company's internet usage.
- Deploy "risk-based controls" for the top 5% of identified users responsible for 80% of web-based risks.
- Stay updated on features from web and SASE vendors like ZScaler and Netskope.


Web Security Health Assessment
- Evaluate the percentage of critical controls currently implemented in your web gateway, and receive tailored recommendations highlighting key controls to activate for enhancing the security of your company's internet usage.
- Deploy "risk-based controls" for the top 5% of identified users responsible for 80% of web-based risks.
- Stay updated on features from web and SASE vendors like ZScaler and Netskope.

Email Security Health Assessment
- Recommend the top email security controls that are currently inactive, accompanied by granular guidance on their implementation.
- Identify specific controls tailored to different functions and departments for activation in your email gateway.
- Evaluate the potential for optimizing your email controls together with your web and endpoint and identity controls.
Identity and Access management assessment
- Optimize utilization and configuration of identity tools such as AD and Okta.
- Identify and categorize risky users through analysis of logs from other security products, placing them into designated "Risky user" categories.
- Identify and activate key available IAM controls to enhance the overall security framework.


Identity and Access management assessment
- Optimize utilization and configuration of identity tools such as AD and Okta.
- Identify and categorize risky users through analysis of logs from other security products, placing them into designated "Risky user" categories.
- Identify and activate key available IAM controls to enhance the overall security framework.

Privileged Access Management Assessment
- Identify and map high-risk privileged access users within your system.
- Implement targeted control changes specifically designed for higher-risk users.
Process improvement recommendations
- Facilitate real-time visibility of control changes for various team members across EDR, Identity, SOC, Operations, and Finance.
- Seamlessly integrate with service management products to monitor and streamline control change processes.
- Track and audit control changes along with the underlying processes to drive improvements.


MITRE driven compliance
- Real-time mapping of all your controls to various MITRE standards.
- Develop informative heat maps linking your controls to both MITRE ATT&CK and MITRE D3FEND, allowing for ongoing progress tracking.
MITRE driven compliance
- Real-time mapping of all your controls to various MITRE standards.
- Develop informative heat maps linking your controls to both MITRE ATT&CK and MITRE D3FEND, allowing for ongoing progress tracking.

We work with a multitude of market leading security solutions