In today's digitally interconnected landscape, cybersecurity investments stand as the sentinel against an ever- evolving array of threats. The integrity and resilience of organizational infrastructures hinge on the meticulous strategies crafted by Chief Information Security Officers (CISOs). CISOs play a pivotal role in fortifying entities against cyber adversaries, ensuring data confidentiality, integrity, and availability. The escalating sophistication of cyber threats underscores the critical importance of judiciously allocating resources to robust cybersecurity measures.

The current landscape of cybersecurity investments
Global spending on cybersecurity products and services is on track to hit a staggering $1.75 trillion between2021 and 2025. Yet, amid this gold rush, CISOs find themselves in a precarious position.
Despite pouring resources into defenses, over 70% confess to feeling like they're throwing darts in the dark, potentially wasting up to a quarter of their budget on ineffective measures.
They are grappling with the formidable task of showcasing ROI and tangible value derived from their cybersecurity tools and investments. As organizations allocate substantial resources to fortify their digital defenses, CISOs navigate the complexities of a dynamic threat environment, where the efficacy of cybersecurity measures is often challenging to quantify.
The current scenario underscores the imperative for CISOs to meticulously assess and communicate the impact of their investments. The diversity of cyber threats, coupled with the proliferation of sophisticated attack vectors, demands a strategic approach to cybersecurity spending. CISOs must align their investment decisions with the organization's risk profile, emphasizing proactive measures to thwart emerging threats.
Amidst this intricate web of challenges, elucidating the true value of cybersecurity investments becomes paramount for CISOs seeking to fortify their organizations against the ever-adaptive nature of cyber adversaries.
Challenges faced by CISOs in demonstrating ROI and value of their cybersecurity investments
Underutilization of security tools
Organizations allocate substantial budgets to cybersecurity tools; however, most of these tools remain underutilized. The inefficiency arises from the lack of optimization in security controls and configurations, failing to adapt dynamically to the evolving threat landscape. Consequently, the effectiveness of these tools is compromised, highlighting the need for a more adaptive and responsive cybersecurity approach.
Fragmented insights from siloed products
Siloed security products fail to provide comprehensive insights into overall progress. The absence of cohesive integration and communication between these products hampers the ability to gauge and demonstrate security advancements effectively. This fragmentation impedes a holistic understanding of the cybersecurity posture of the organization, emphasizing the importance of interconnected solutions for a more insightful and unified view of organizational security progress.

Lack of cybersecurity metrics and benchmarking
The absence of standardized metrics makes it difficult to articulate the true impact of the cybersecurity initiatives to stakeholders. The challenge lies not only in defining meaningful cybersecurity metrics but also in aligning them with recognized benchmarks, hindering the ability to effectively track progress and communicate advancements in a universally understood manner. Establishing such benchmarks becomes imperative for organizations to demonstrate the tangible value of their cybersecurity investments.
Technology Obsolescence
Rapid technological advancements can quickly render security solutions obsolete, impacting the long-term value of investments. CISOs can mitigate this by implementing a proactive scorecard system to measure and ensure the ongoing effectiveness of security tools.
Difficulty in Quantifying Cybersecurity Risk Reduction
Measuring the reduction in cybersecurity risks can be a complex task. CISOs often struggle to quantify how specific security measures have contributed to risk reduction, making it challenging to demonstrate the tangible impact of their investments to key stakeholders. Developing effective risk reduction metrics and methodologies becomes crucial for conveying the value of security initiatives.
Limited Alignment with Business Objectives
Security investments may not always align seamlessly with broader business objectives. CISOs face the challenge of demonstrating how cybersecurity initiatives directly contribute to the overall success and
profitability of the organization. Establishing a clear link between security investments and business goals is essential for showcasing the strategic value of security measures.
Limited Understanding of Cybersecurity by Non-Technical Stakeholders
Communicating the value of security investments to non-technical stakeholders can be challenging. CISOs often struggle with translating technical details into business language that resonates with executives and board members. Bridging the communication gap and presenting security outcomes in a way that aligns with the broader organizational strategy is essential for gaining support and demonstrating value.
Measuring cybersecurity ROI
Measuring the Return on Investment (ROI) of cybersecurity initiatives is crucial for CISOs and security professionals to demonstrate the tangible value of their efforts. Adopting effective methodologies and utilizing relevant metrics is essential in quantifying the impact of cybersecurity investments.
Crafting a Visual and Strategic Approach to showcasing cybersecurity ROI
Personalized Dashboards: Tailored dashboards for different stakeholders, including executives, IT teams, and compliance officers, allow them to visualize and comprehend the ROI based on their specific interests and responsibilities.
Mapping with Frameworks: Aligning cybersecurity initiatives with established frameworks like MITRE ATT&CK and CIS Controls helps track progress systematically, ensuring that security measures address recognized threats and vulnerabilities.
Usability Metrics: Evaluating the efficacy of current investments and tools involves measuring their usability. Metrics such as Time to Detect and Respond to Threats and User Satisfaction can gauge how well these tools contribute to the organization's overall security posture.
Cybersecurity Mesh Integration: Recognizing the need for a holistic approach, organizations are adopting a Cybersecurity Mesh to interconnect diverse security tools. This integration fosters consolidated insights, facilitating a unified view of the threat landscape and providing actionable recommendations. This approach enhances the organization's agility in responding to evolving cyber threats.
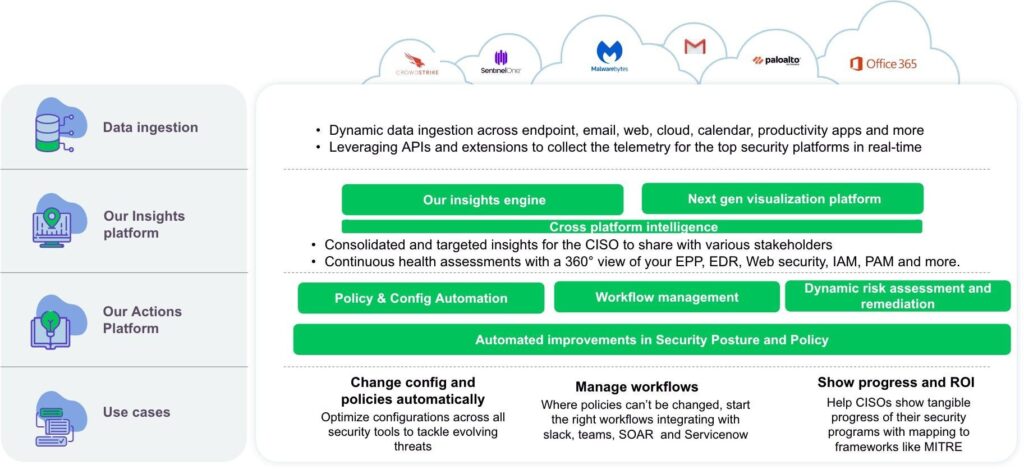
Discern's AI powered cybersecurity mesh leverages APIs to collect the telemetry from your top security platforms in real-time to bring you curated insights and actionable recommendations.
Methodologies and Metrics
One effective methodology is the Risk-Adjusted Return on Investment (RAROI), which considers the potential risk reduction and financial impact of security measures. Metrics such as the Cybersecurity Maturity Model Certification (CMMC) score and the Number of Incidents Post-Investment provide quantifiable insights into the effectiveness of cybersecurity strategies.
Key Performance Indicators (KPIs) play a pivotal role in assessing the effectiveness of cybersecurity investments. Examples of relevant KPIs include:
Incident Response Time: Measuring the time taken to identify and respond to security incidents provides insights into the organization's ability to contain and mitigate threats swiftly.
Detection Rate: Monitoring the efficiency of security tools in detecting and preventing threats helps evaluate the overall strength of the cybersecurity infrastructure.
Phishing Resilience: Assessing the organization's susceptibility to phishing attacks and tracking the improvement in employee awareness and responsiveness is a critical KPI.
Risk Reduction: Quantifying the reduction in cybersecurity risk is essential for showcasing the impact of security measures on minimizing the likelihood and potential impact of security incidents.
Compliance Adherence: Ensuring compliance with industry regulations and standards is a measurable indicator of the organization's commitment to robust cybersecurity practices.
Downtime Reduction: Measuring the decrease in system downtime resulting from cybersecurity
measures helps quantify the financial benefits of avoiding disruptions to business operations.
Cost of a Data Breach: Evaluating the financial impact of a potential data breach and comparing it to the investment in cybersecurity provides a clear understanding of the ROI.
Aligning Security with Business Goals
The symbiotic relationship between cybersecurity initiatives and overarching business objectives is no longer a mere aspiration but a strategic imperative. The alignment of cybersecurity with business goals is a linchpin that not only fortifies digital fortresses but propels organizational success through optimized ROI.
Define Clear Business Objectives:
Begin by articulating and delineating the precise business objectives that the organization aims to achieve. This could include market expansion, revenue growth, regulatory compliance, or operational efficiency.
Map Cybersecurity Initiatives to Business Objectives:
With defined business goals, map out specific cybersecurity initiatives that directly support and enhance each objective. This step involves a granular understanding of how security measures can act as enablers rather than inhibitors to business pursuits.
Integrate Risk Mitigation into Operational Workflows:
Execute the integration of risk mitigation strategies seamlessly into operational workflows. This involves embedding security protocols into everyday processes to ensure a proactive and continuous defense against potential threats.
Leverage Compliance Measures as Business Assurance:
Align cybersecurity efforts with industry regulations and compliance standards. Use compliance not just as a checklist but as a strategic tool to assure clients, partners, and stakeholders of the organization's commitment to robust security practices.
Foster a Culture of Secure Innovation:
Actively promote a culture where cybersecurity is not a hindrance to innovation but a catalyst. Enable secure innovation environments, ensuring that creative endeavors are shielded from potential risks, thereby fostering a dynamic and secure organizational ecosystem.
Continuous evaluation and adaptation of cybersecurity tools and products:
Continuous evaluation and adaptation of cybersecurity tools and products emerge as pivotal practices, offering CISOs a pathway to not only bolster their organization's defense but to extract maximal ROI from their cybersecurity endeavors.
Anticipation of Evolving Threats:
Continuous Threat Intelligence Integration: Regularly updating and integrating threat intelligence feeds allows for proactive identification and mitigation of emerging threats.
Dynamic Vulnerability Assessments: Regular assessments ensure that cybersecurity tools are adept at identifying and remedying vulnerabilities in a rapidly evolving threat landscape.
Optimizing Technology Stack:
Regular Vendor Assessment: Continuous evaluation of vendors ensures that cybersecurity tools align with evolving organizational needs and industry benchmarks.
Integration of Cutting-Edge Technologies: Embracing emerging technologies ensures that the technology stack remains resilient and capable of addressing novel threat vectors.
Agile Response to Incidents:
Regular Simulation Exercises: Conducting regular incident response simulations aids in identifying gaps in the cybersecurity infrastructure, enabling refinement for more effective responses.
Adaptive Incident Forensics: Continuous refinement of incident forensics capabilities ensures precise
identification and mitigation of security incidents, minimizing potential damage.
Ensuring Usability and User Training:
User-Centric Design: Evaluating the usability of cybersecurity tools ensures that they are user-friendly, reducing the likelihood of errors and enhancing overall efficiency.
Continuous Training Programs: Regular training programs foster a culture of cybersecurity awareness,
ensuring that end-users are equipped to make informed decisions and minimize security risks.
Benchmarking Against Industry Standards:
Alignment with Regulatory Changes: Continuous evaluation ensures that cybersecurity measures align with evolving regulatory requirements, reducing compliance risks and associated costs.
Adherence to Industry Best Practices: Benchmarking cybersecurity strategies against industry standards
ensures that the organization's security posture remains at the forefront of best practices.
Conclusion:
CISOs today face formidable challenges in showcasing ROI amidst escalating threats. Despite soaring global investments, issues like underutilized tools and communication gaps persist. To overcome these hurdles, a strategic alignment of cybersecurity with business objectives is essential. Visual approaches, metrics like RAROI, and continuous evaluation practices offer pathways for tangible ROI demonstration. As organizations navigate a complex threat landscape, CISOs must ensure their cybersecurity measures not only fortify defenses but also contribute seamlessly to overarching business success, fostering resilience and adaptability in the face of evolving cyber adversaries.





